The phrase "many eyes gives better security" works in the open source world extremely well ... as long as you can make sure that all parts of the security model are available for independent review.
As soon as you hide any part of that, the "many eyes" security model no longer applies. Docker hides part of that process when they create the docker image and do not make available the vendor image from which the docker image was created.
Let's look at Ubuntu as an example: Ubuntu puts out a 5 image rolling vendor release of a system at https://partner-images.canonical.com/core/ which Docker uses to create the docker image. Lets look at the canonical site today 2021-04-14.
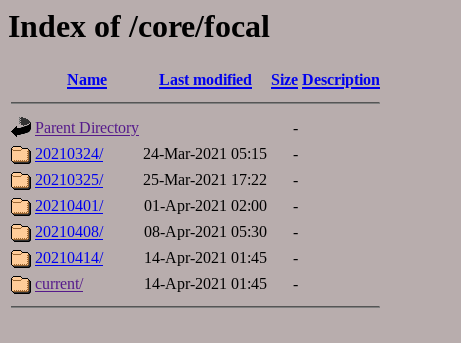
Now let's look at docker's image:
$ sudo docker pull ubuntu:focal
focal: Pulling from library/ubuntu
Digest: sha256:3c9c713e0979e9bd6061ed52ac1e9e1f246c9495aa063619d9d695fb8039aa1f
Status: Image is up to date for ubuntu:focal
docker.io/library/ubuntu:focal
$ sudo docker inspect ubuntu:focal | grep Created
"Created": "2021-04-03T00:53:09.625644166Z",
$ sudo DOCKER_CONTENT_TRUST=1 docker pull ubuntu:focal
Pull (1 of 1): ubuntu:focal@sha256:c95a8e48bf88e9849f3e0f723d9f49fa12c5a00cfc6e60d2bc99d87555295e4c
sha256:c95a8e48bf88e9849f3e0f723d9f49fa12c5a00cfc6e60d2bc99d87555295e4c: Pulling from library/ubuntu
Digest: sha256:c95a8e48bf88e9849f3e0f723d9f49fa12c5a00cfc6e60d2bc99d87555295e4c
Status: Image is up to date for ubuntu@sha256:c95a8e48bf88e9849f3e0f723d9f49fa12c5a00cfc6e60d2bc99d87555295e4c
Tagging ubuntu@sha256:c95a8e48bf88e9849f3e0f723d9f49fa12c5a00cfc6e60d2bc99d87555295e4c as ubuntu:focal
docker.io/library/ubuntu:focal
$ sudo docker inspect ubuntu:focal | grep Created
"Created": "2020-11-25T22:25:29.546718343Z",
Notice that the version with DOCKER_CONTENT_TRUST=1 is made with a version that is no longer available for verification.
I find this concerning, not just because Ubuntu is one of the most popular docker repos, but because many other popular repos (e.g. NVIDIA) use the docker Ubuntu image as their base as well.
So this means as a security verification step, when we identify the version that Docker uses for their base image, we have to store and record the hash information for the underlying base image separately because otherwise this allows for a number of attack vectors that can occur without being seen/detected should a hostile entity attack a hosted docker image.
- Log in to post comments